Secure your connected devices today
Contact us today to discuss your specific cybersecurity needs and secure your connected devices against potential threats.
For robust protection, secure your IoT, wearables, and sensor devices against cyber threats using trust anchors, FUOTA, Encryptflow, and post-quantum cryptography.

In the wake of the digitalization revolution, small, embedded devices with various forms of wireless connectivity have been integrated into consumer products, infrastructure, and manufacturing machines, or have given rise to new concepts altogether, such as personal wearable devices. The potential of this paradigm, sometimes called the Internet of Things (IoT), is enormous: the collected data can produce valuable insights, support informed decisions, enable timely action, and sometimes even carry out the action.
However, with their connectivity and inclusion in large-scale applications, these devices also become exposed to cyberattacks. Security in the IoT is especially precarious due to a tension between the low cost and constrained features of the devices on one hand and the potentially hostile environment in which the devices are deployed on the other, with attacks and vulnerabilities having been documented. Designing and implementing an effective cybersecurity concept for an embedded device thus needs to consider all possible attack vectors and be driven by the threat landscape specific to the given application.
To help organizations tackle this issue, CSEM has built up expertise to, on the one hand, secure end devices with trust anchor and firmware updates over the air (FUOTA) and, on the other, bolster control and security on data with Encryptflow, CSEM's state-of-the-art technology for data exchange.
Finally, CSEM also paves the way for next-generation Post Quantum Cryptography (PQC) to ensure devices are secured when quantum computers become available.
Whether you are a startup or an established industry professional, we provide the expertise and technology required to secure your connected devices. Recently, CSEM has supported E-Chronos to enhance the security of their radio controls for heavy machineries.
Once a fleet of embedded devices has been deployed, it can be very difficult to maintain it in a way that is logistically and economically scalable. The key enabler for such scalable fleet maintenance is transferring new, improved versions of device firmware to the fleet over the network, without the need for ad-hoc intervention.
Many cautionary tales illustrate the unpleasantness of an ineffective FUOTA. They include customers having to replace a product with a newer, patched version or technicians having to perform manual firmware updates in the field on millions of devices.
Because attackers targeting connected IoT devices can combine both remote and physical attacks to great effect, evaluating the actual security of various secure boot and firmware update solutions is not an easy task. In collaboration with EPFL, CSEM has defined a formal security model, allowing various solutions to be rigorously analyzed.
This security model is based on the well-established methodology of “attack games”. The attacker, modeled as an arbitrary algorithm with substantial but still finite computational resources, plays one of three games, each of which models a fundamental security property of FUOTA and secure boot:
In each of these games, a simplified, mathematical model replaces the embedded system and the attacker is allowed to freely and adaptively perform one of a small number of possible interactions with the model device in a sequence. These simulations allow a rapid identification of potential security vulnerabilities.
When implemented in a particular device, however, attention to detail is needed to achieve the desired security, efficiency and robustness.
To help innovators secure their devices, CSEM has implemented secure boot and FUOTA in a number of embedded platforms, such as the STM32 and Nordic nRF52 families, based on the popular MCUboot open-source framework. The solution is flexible and has been adapted to a variety of systems, from simple devices designed from scratch to projects with legacy constraints or to more complex multi-SoC systems. The secure bootloader can be as small as 16kB and examples of integration into Continuous Integration and Continuous Deployment(CI/CD) are available. The solution has also been verified with our formal security model in order to avoid nasty surprises.
Wearables, such as the Tissot T-Touch Solar Connect smartwatch, contain multiple microcontroller units. Their updates require customized scenarios.

The EncryptFlow, a technology for end-to-end data encryption with built-in, granular data sharing and audit trails, is particularly relevant to medical data.
As the main driver of technological progress and economic growth in the modern digital economy, data generates value by being transformed into insights, applications, and services. But this potential often remains undeveloped because factors such as a data ownership mindset or the limitations of current data management systems split data into silos. This isn’t helped by the fact that a regulatory framework on data sharing is still under construction.
Responding to this, CSEM has designed a unique technology called EncryptFlow. It integrates end-to-end data encryption and transparent data sharing, enabling a data owner to retain fine-grained control over who gets what access. EncryptFlow is also designed and optimized to scale up to IoT proportions. The full interaction in a transaction is automatically embedded in a signed, sequential, and non-repudiable audit trail, available to both parties in the exchange.
EncryptFlow is compatible with data generation in resource-constrained devices, with the data encryption module taking up less than 10kB of ROM and requiring 2kB of RAM in total. At the same time, a compact key manager can provision (hundreds of) thousands of such data encryption modules with initial keys and subsequent reconstruct decryption keys. Combined with cryptography, EncryptFlow ensures integrity of both the data being shared and the full exchange. Thanks to portable microledgers, the technology can be used on its own, or integrated with a distributed ledger or trusted execution environments for various tradeoffs between data protection guarantees, overhead, and portability.
Quantum computers will render the current industry-standard public key cryptography insecure. US government contractors must use the new Post-Quantum Crypto (PQC) standard as default from 2025 and fully switch to PQC by 2035. Europe is following.
Making an IoT fleet post-quantum ready implies a backward, non-compatible replacement of cryptographic keys and implementations in all devices. CSEM is designing the software, the hardware and other supportive technologies for a smooth post-quantum IoT transition deployed over the air, minimizing costs and complications.
Post-Quantum Crypto Transition
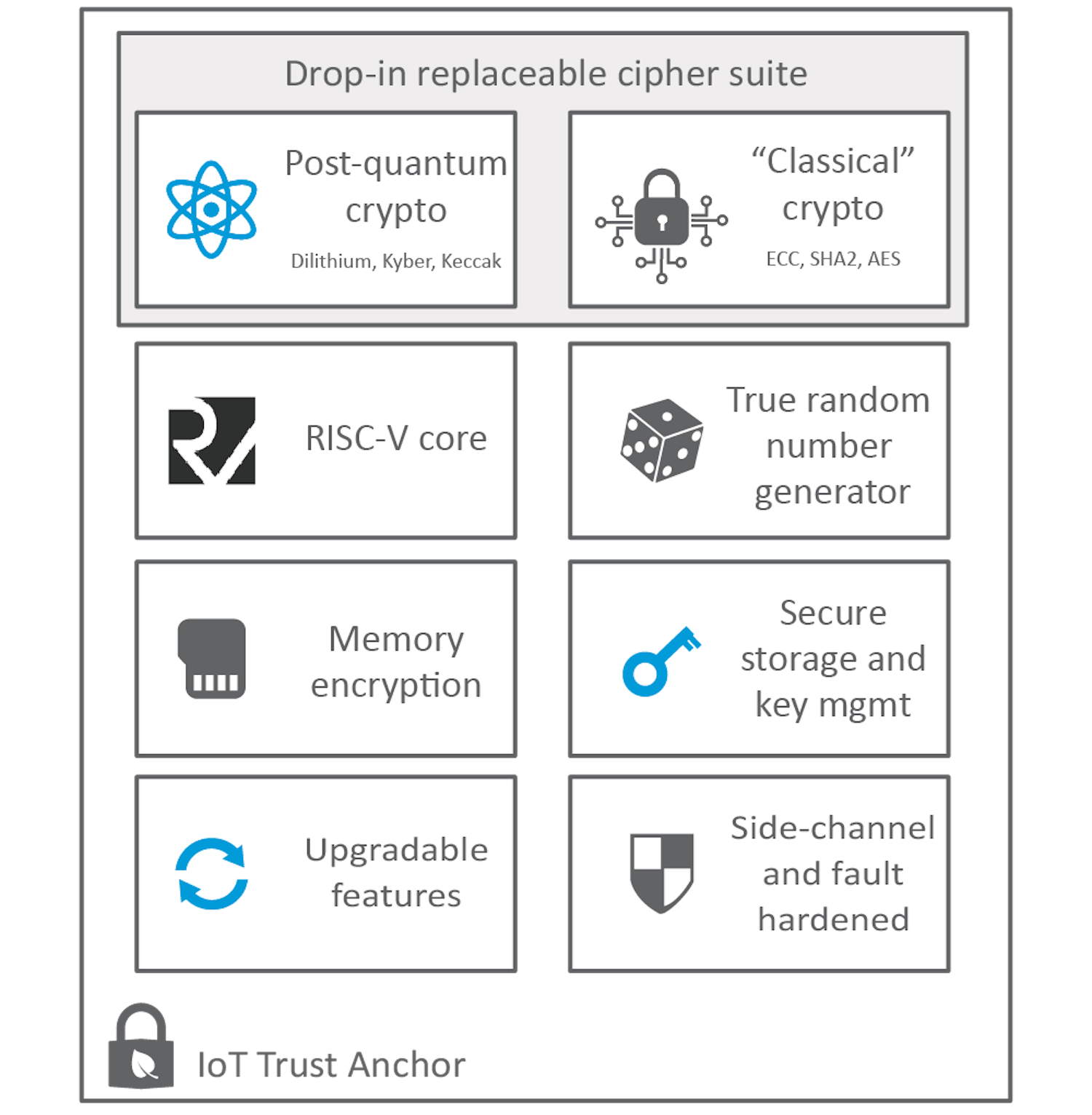
CSEM’s proposed solution is a low-footprint Trusted Anchor (TAn) (hard macro and associated firmware) offering state-of-the-art cryptographic accelerators designed to resist low-skilled to medium-level attacks (e.g., AVA_VAN2/3) throughout the lifespan of a typical low-cost IoT solution.
Our RISC-V-based TAn primarily targets applications where resources are scarce, such that conventional defenses against power analysis and other side channel attacks would be prohibitively costly, delivering more aggressive, yet well-analyzed cost-security trade-offs.
The TAn is designed to be future-proof from the ground up. This includes acceleration of Post-Quantum secure cryptography and, and, unlike conventional secure elements, fully embraces the support of both firmware updates and partial hardware reconfiguration, in alignment with the paradigm of crypto-agility. As a result, our TAn embeds the necessary tools to secure IoT solutions over a long life span (≥ 20 years). We would love to hear your thoughts!
To support PQC transition in legacy systems and COTS platforms, a software variant of the TAn relying on platform SW isolation features, such as ARM TrustZoneM, is being developed as well. It packs all the essential features of post-quantum-security and crypto-agility but lacks the low-overhead side-channel defenses, the acceleration capabilities, and enhanced isolation of the hardware-base TAn incarnation.
Contact us today to discuss your specific cybersecurity needs and secure your connected devices against potential threats.
Secure Boot and Firmware Update for μ111 RTOS, D. Vizár, I. Ben Salah, A. Ferragni, CSEM Scientific and Technical Report 2021, p. 19
Securing Embedded Firmware Update over the Air with Distributed Encryption D. Vizár, M. I. Ben Salah, Q. Liang, CSEM Scientific and Technical Report 2023, p. 22
Threshold Signatures for Embedded Platforms, D. Gallay, A. Duc , D. Vizár CSEM Scientific and Technical Report 2023, p. 35
A Key Management Framework to Secure IoMT-enabled Healthcare Systems, De Ree, M., Vizár, D., Mantas, G., Bastos, J., Kassapoglou-Faist, C., Rodriguez, J., IEEE 26th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), 2021, pp. 1-6. (access to this document requires a subscription.)
Discovering Vulnerabilities in Embedded Firmware with Fuzzing Techniques, Vizár, Damian, Ben Salah, Mohammed Ismail, Marty, Mathias, CSEM Scientific and Technical Report 2023, p. 32
Instruction Set Extensions for Post-Quantum Cryptography, Brohet, Marco, Valencia, Felipe, Regazzoni, Francesco, 2023 IEEE/ACM International Conference on Computer Aided Design (ICCAD), San Francisco, CA, USA, 2023, pp. 1-6. (access to this document requires a subscription.)